LEVEL 6
Task
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
Username: bandit4
Password: string provided in the human-readable -file07 file in the previous level
Theory
From Level 5, I now know that human-readable means a file with a common data encoding of either ASCII text and Unicode. So these are the two file types I’ll have to search for.
The new parameters here are the file size and that it’s not executable. So my plan is to work through this task step-by-step where I’ll find human-readable files, then narrow it down to the file size and finally non-executable files.
I’ll share my write-up below (along with my thought process). This will be a slightly longer post than usual because it took me quite a while. I later found a more concise solution that I’ll share at the end of this post.
Solution
Step 1: As usual, I changed to the inhere directory
I used ls -la to list out the contents of the directory. Damn, there’re multiple folders! And I know they’re folders because it says root.
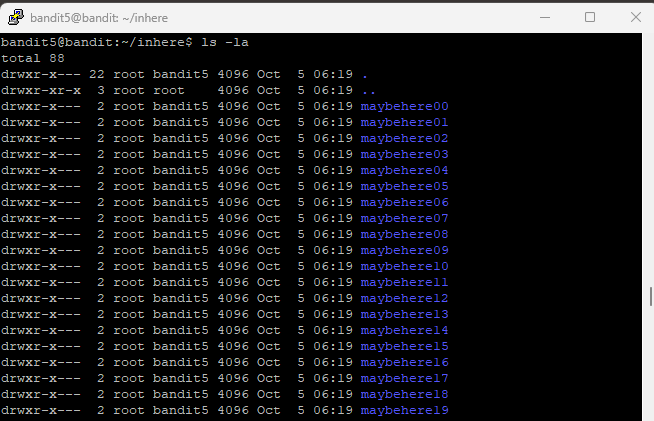
Step 2: Maybe I’ll try my luck and get an overview of individual folders. I choose maybehere07 (because it’s my lucky number) and maybehere18. No such luck. Both folders have multiple files within them.
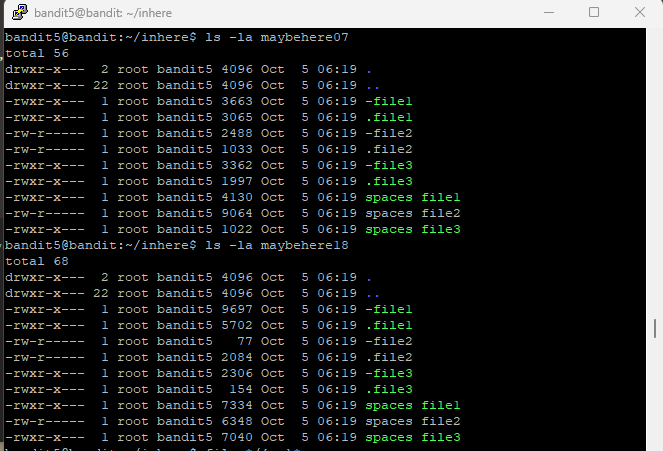
Step 3: Instead of looking into every directory, what if I list all files in all directories/folders? In the previous level, the command file will list the file type. So using the command file */* will return all file types in all directories.
However, this does not match hidden files. After a bit a research, I found a command that might work file */{.,}*, where it will list out all hidden files and non-hidden files starting with anything else.
Substack lifesaver link. That’s still a lot of files but at least we’re getting somewhere.
Step 4: From the previous level, I know that human-readable files are ASCII text files. Now I need to filter out those files. In a cybersecurity workshop I attended, I know I can use the | pipeline and the grep in my command. Pipe and Grep in Linux.
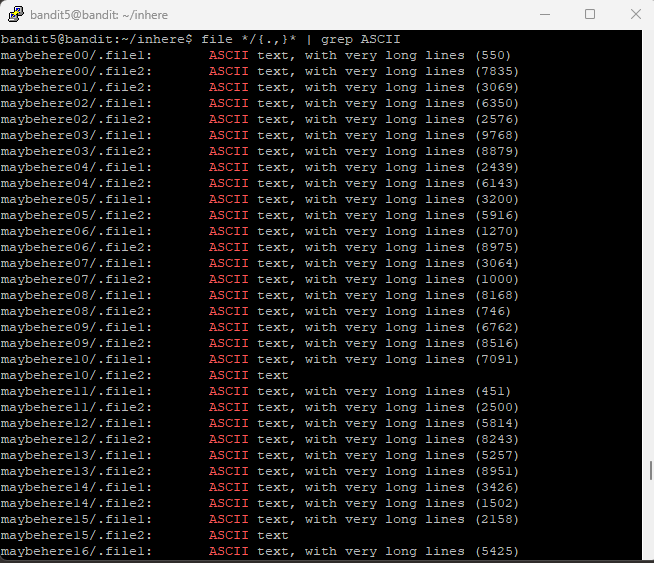
I use the command file */{.,}* | grep ASCII. Now we’re getting warmer
Step 5: Based on the previous level, the password string was located in a ASCII text file. So we have to filter our command even further.
I use the commmand file */{.,}* | grep ASCII | grep -v ", with very long lines". The -v flag will exclude the indicated line. I have to add quote marks around the line to indicated that all the words belong to one line.
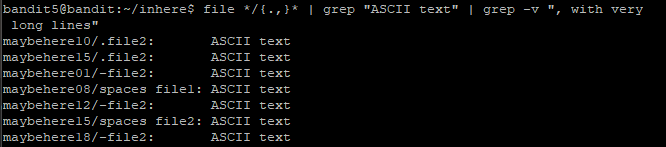
Step 6: As mentioned in the task, the file is 1033 bytes in size. So I used the command file */{.,}* | grep ASCII | grep -v ", with very long lines" | grep 1033c. The c at the end stands for bytes. I keyed in the command but nothing return. Drats.
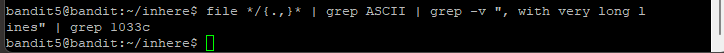
Step 7: Time to backtrack a bit. What if I use du to get the sizes of all files in all directories? I can then further refine the command with grep 1033. To do this, I key in the command du -a -b | grep 1033. As shown in Level 4, -a will list the hidden files too. -b is to show the files in bytes.
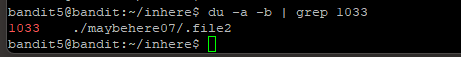
Step 8: Time to use cat to read the file’s content. I found the password string!! However, it means my previous process was incorrect as this file didn’t even appear in the list in Step 5.
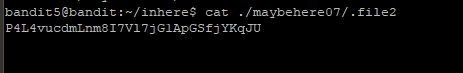
Reflections
I did use the find . ! -executable command to find non-executable files. But again I got a long list of files that didn’t help to narrow down my search.
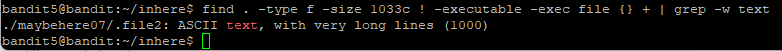
So after completing the task, I wondered if there was a single command that could help to narrow down to a file that fits all three criteria. After researching online, I found a command that works: find . -type f -size 1033c ! -executable -exec file {} + | grep -w text, providing the same file in Step 8. Single command
-type fto look for only files-size 1033cto look for only file size of 1033 bytes! - executableto look for only non-executable files-exec file {} +, where-execexecutes the command. This link explains what{} +does, something I’m still trying to understand.-w textwill only print lines where the text is a standalone word, which the password string is.
Level 6 completed. Definitely much more logical and procedural thinking involved.